As described, the system needs to be secure, so the goals are:
- During normal operation, no network ports on the device should be open
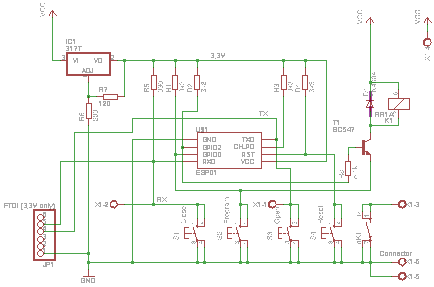
- The device should connect to an MQTT broker using TLS encryption
- The device needs to verify the host that it is connecting to is who it says it is
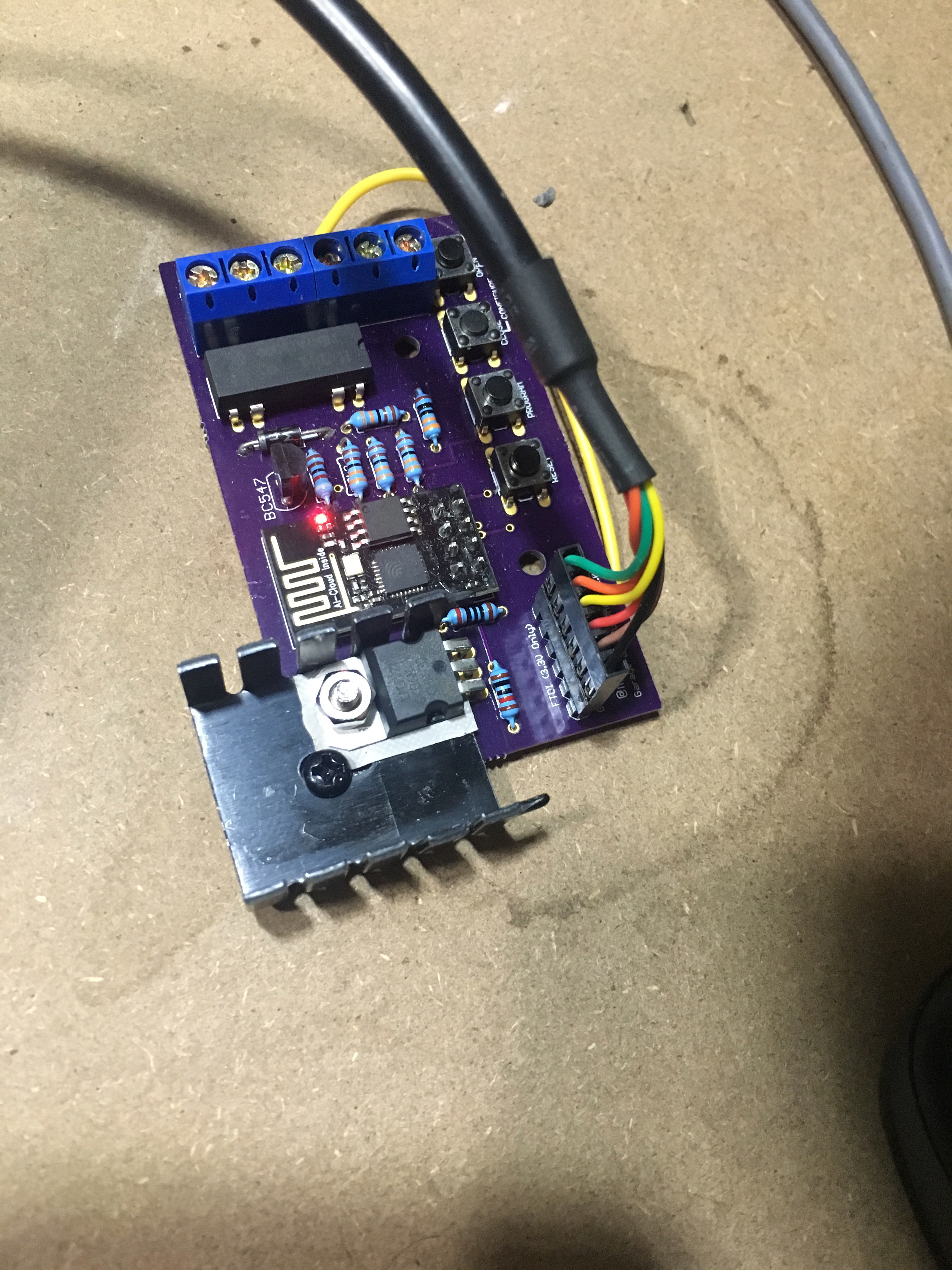
- Configuration will be done via a captivate portal that will only be created when physical buttons on the device are pressed.
I'm planning on integrating the device with a locally-running copy of Home Assistant. Ideally I can get the homekit integration working, so I can ask Siri to open it via my Apple Watch.
I want to the build to look like a finished piece, so I'm going to design a custom PCB for it.
I also want to investigate building a user-friendly, usable, well designed single-page web app for the captivate portal configuration screen. The design goals for this part are:
- Due to the limited resources on the device, the HTML, CSS and JavaScript should be as small as possible. This means no libraries, heavy minification tricks and pre-gzipping of the web page.
- Useability is the highest priority, followed by size, followed by speed. Browsers run on powerful computers, so they can do a bit more work if it means shaving size off the deliverable.
- Ideally it should be bundled as part of the firmware, and not as a binary blob uploaded to the ESP8266 filesystem.
- It should require no external network assets - everything delivered must live on the ESP8266.
 Myles Eftos
Myles Eftos

You do not so much need a heatsink, you need a step down regulator. :-)
If you want to stay with the linear approach then you could improve your calculation of the thermal resistance.
* At first do not use an "average" ambient temperature, use the worst case, that is the highest temperature you want your device to work reliable. Lets say 40°C. Take a rise of the temperature in the enclosure into account.
* Second take the internal thermal resistance of the package (junction to case[bottom, mounting plate]) into account, but that is only 1.1K/W for the TO220.
* Then take the maximum allowable junction temperature, for the normal LM317 that is 125°C
Now you get an allowable rise of the junction temperature of 125-40=85°C. With a dissipation of 2,784W you get an allowable sum of thermal resistances of 85/2,784 = 30,53K/W. From this you can subtract the internal therm. res. and additional 0,5 to 1K/W for the thermal interface materials (heat sink grease, mica or silicone). So your heatsink has to be 28,5K/W or better (Lower).