Some ressources to be update on the go
ESP NOW protocol:
https://docs.espressif.com/projects/esp-idf/en/latest/api-reference/wifi/esp_now.html
http://wiki.ai-thinker.com/_media/esp8266/docs/30c_esp-now_user_guide_en.pdf
Linux Wireless Networking:
https://www.linux.com/blog/linux-wireless-networking-short-walk
After swimming in a lot of information, I think I found the perfect starting point to send and receive raw 802.11 packet !
https://warmcat.com/git/packetspammer
Update 12/14/2018: Here is an other lib to send and receive raw wifi packet, It even has a python binding...To be tested soon..
https://github.com/kismetwireless/lorcon
Update 03/01/2019: The useful information was here
https://www.kernel.org/doc/Documentation/networking/mac80211-injection.txt
 Thomas Flayols
Thomas Flayols
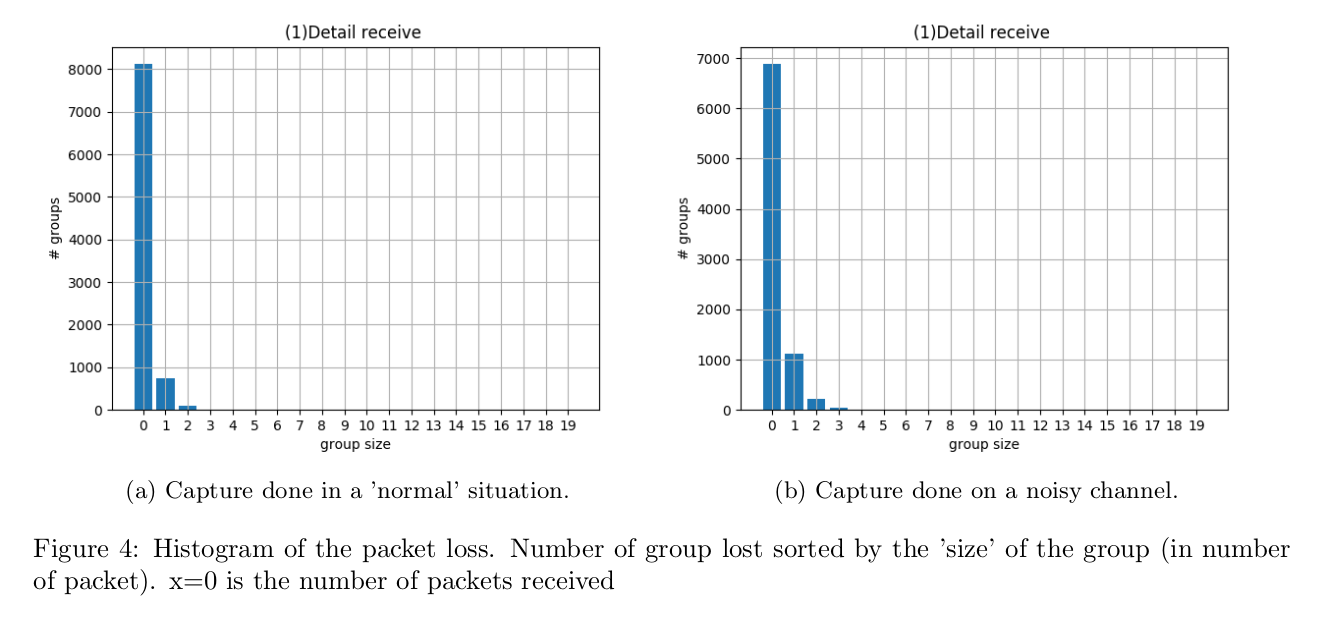






 Kevin Kessler
Kevin Kessler
 Dan Fay
Dan Fay
 lpauly
lpauly
 Thorsten von Eicken
Thorsten von Eicken
So what is the benefit of using this over websockets?