So I have started up work on this again, and from learning new things with other projects I have been able to better move forward on this project.
The bad news is that the index page to the AWS site has been locked, so now I can't navigate to find new firmware files.
The good news is that I have made a lot of headway with learning Ghidra and reverse engineering the STM32 series MCU's. With this I have been able to make good headway in understanding the MCU firmware on some of the higher end Shark models that utilize SLAM navigation. These units utilize the STM32F3 Cortex-M4 MCU where as the models I am working with use the STM32F0 Cortex-M0 MCU.
With the RV750N & RV850 models, the MCU used is also the STM32F0, and is more closely related to the original RV750. Of the files I was able to scrape from the AWS portal, I was able to determine the model line for the RV750N and RV850, and download firmware images for these models. The problem I am running in to with these images is that they are in a format that currently cannot be decompiled. I have been able to make some sense out of some common constant sections of what I figure is the header.
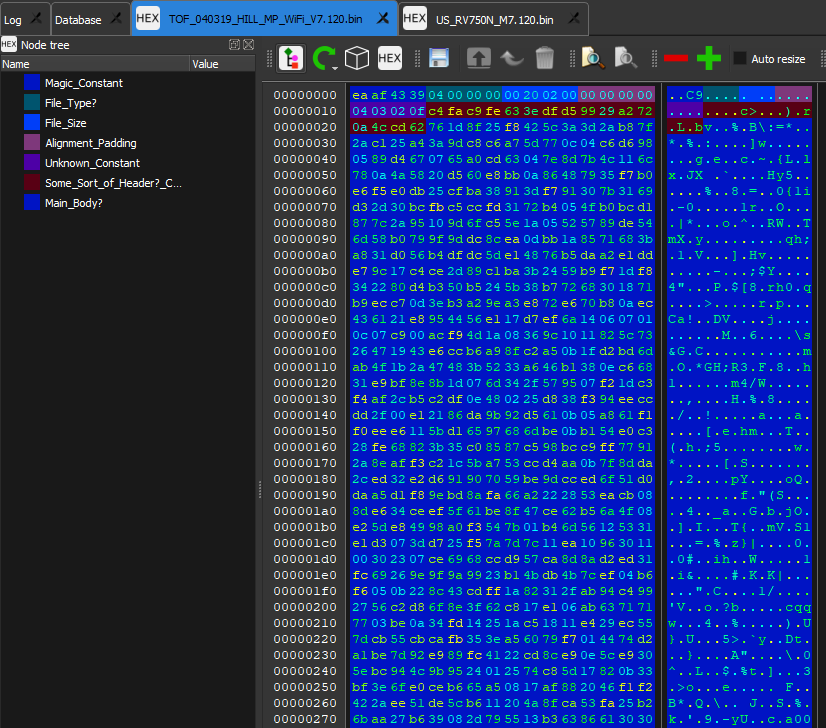
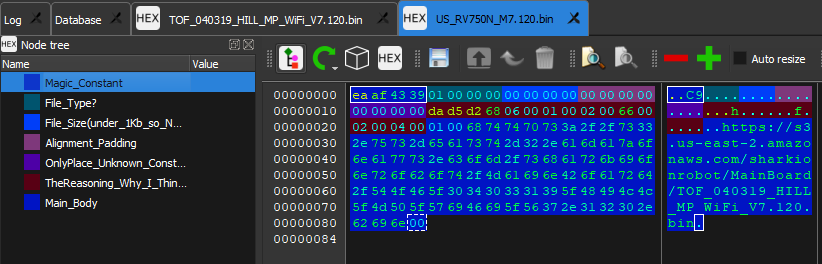
Looking at the the above Hex, The "Some Sort of Header" section I am guess since in the file that points to this file, this area is a data section before an ascii string.
Trying to cross reference the information found in these files to any other firmware format used in the STM32 line has been hopeless. I don't think the firmware is heavily obfuscated since there are sections of repeating byte sequences in some parts of the image. Here is one segment starting at 0x4418 and repeats 33 times.
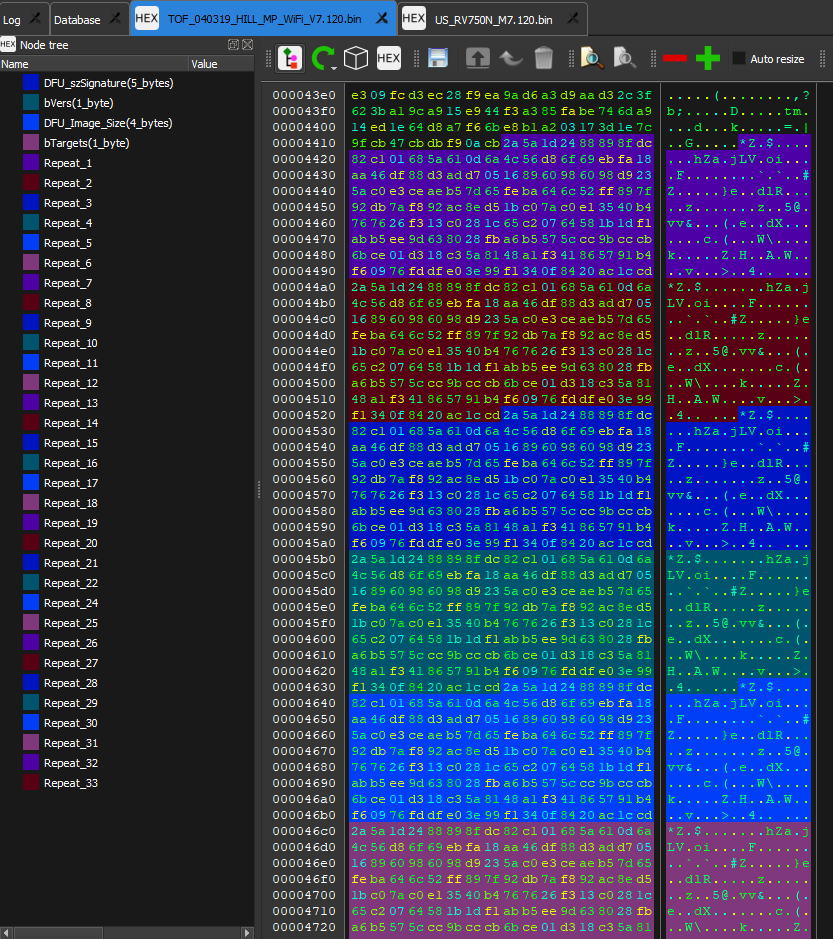
I have tried treating this section as if it supposed to be padded 0x00 or 0xFF, and using it as a key for XOR the file, but it has not worked. There is also another section near the end of the file from 0x1FD90 to 0x21F8F. From the end of this section until the last 16 bytes of the file is undecipherable data, but the last 16 bytes are always constant, and are the value 0x6CA48E4F9E9F5D9301A36C43962C0C95.
And this is where I am at. I do have a mainboard from a Ecovac Deebot N79 coming in, as it seems to be of the same design style... We will see if the firmware can be extracted.
 Jon Steel
Jon Steel
Discussions
Become a Hackaday.io Member
Create an account to leave a comment. Already have an account? Log In.