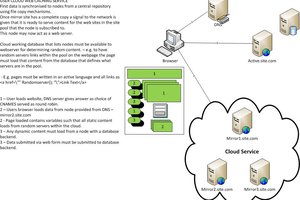
When I moved in to my brand new apartment in a newly constructed high-rise, I was intrigued - it was designed with smart home functionality in mind and every light, power socket, window blind was remote controlled in addition to push-buttons placed around the rooms. Also all HVAC and bathroom floor heating functions were interfaced as well. Besides the DIN-rail mounted relays and PLCs the heart of the user interface was a wall-mounted tablet: every one of the 128 apartments had a Galaxy Tab 3 10.1 P5210 configured with Android apps for smart home control, apartment doorbell and IP intercom. We were given a basic user interface manual but no technical docs, so I set out on figuring how it all works.
Hacking old Galaxy Tabs for better living
How I helped my high-rise neighbors to actually own their smart homes

 Danny
Danny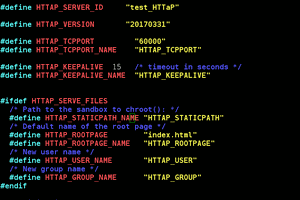
 Yann Guidon / YGDES
Yann Guidon / YGDES
 Hyr0n
Hyr0n
hell yeah, this is great reading, thank you