Step 1: The biggest weakness: GSM and wireless jamming


All alarm systems work like this: first they detect a breach, and they sound the alarm / call or message a security company.
An attacker can try to block the detection (we'll be covering that next) or he can try block the transmission of the message to the security company.
Unfortunately you don't have to be a scientist or a mad engineer to build a device that jams wireless or GSM signals, you can buy them! These devices are legal and are used to protect VIPs or to stop students from cheating at an exam using their cell phone. There are some companies that sell this stuff and the prices are affordable 300 - 1500 $, if you're curious just google "gsm jammer".
So the main thing that an alarm system relies on can be blocked, hmm what can you do?
Ways to protect:
1. the best way would be to avoid this is to use an alarm that supports an ethernet cable and sends email or other alerts via the internet. But for this to be secure the internet cable must not be in reach (should be buried or concealed)
2. install the alarm central unit in the middle of the house, so that the jamming device is less effective due to distance. These devices work up to a distance, the cheapest about 15 meters, the most expensive up to 150 m, at least that's how they are advertised
3. don't keep high value goods in the house, or if you need to ensure them. Thieves that know you have a lot of valuables in the house might go to the trouble of purchasing this kind of equipment
Step 2: Cloning wireless signals
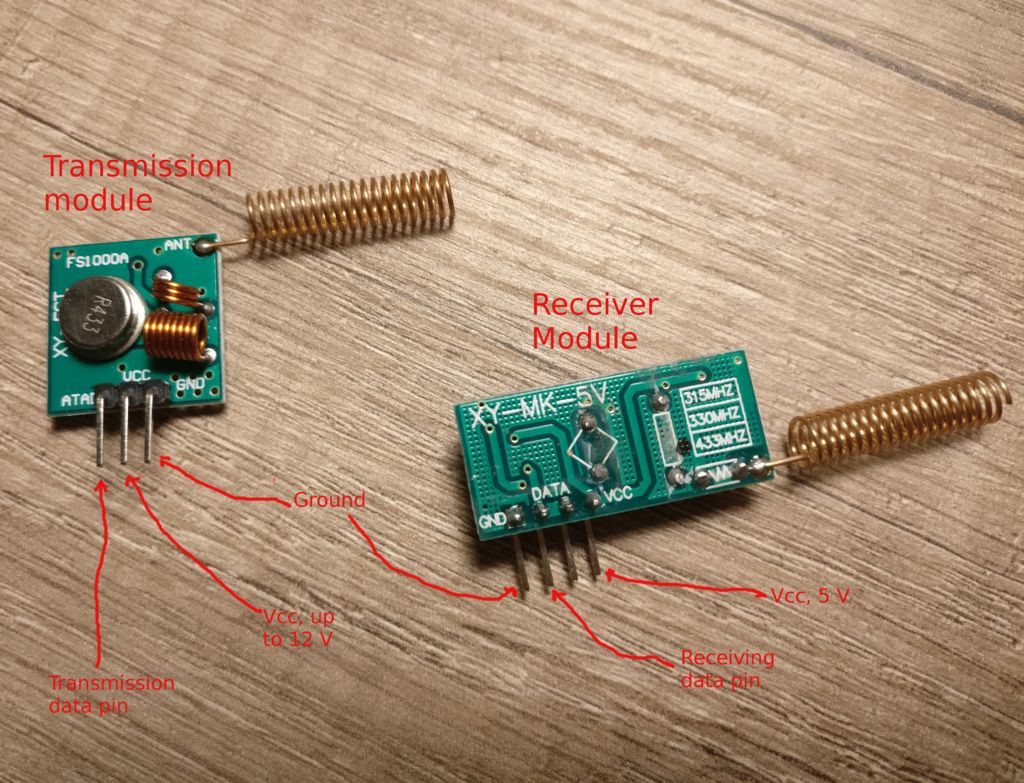

Usually alarms and other RF electronics have 2 main frequencies 315 Mhz and 433 Mhz, the signalis usually modulated FSK or ASK.
FSK (frequency shift keying) modulation means that the signal is encoded by rapid changes in frequency (0 has a frequency, and 1 has some other close frequency)
ASK (amplitude shift keying) modulation means that the signal is encoded by changes in amplitude (no amplitude for 0, max amplitude for 1)
In my test the alarm system is using 433 Mhz ASK modulation (the most common), and i'll try to copy and clone the signal with an Arduino Uno and two modules, one for receiving 433 Mhz signals and one for transmitting them. The modules can be found on eBay for under a dollars per pair.
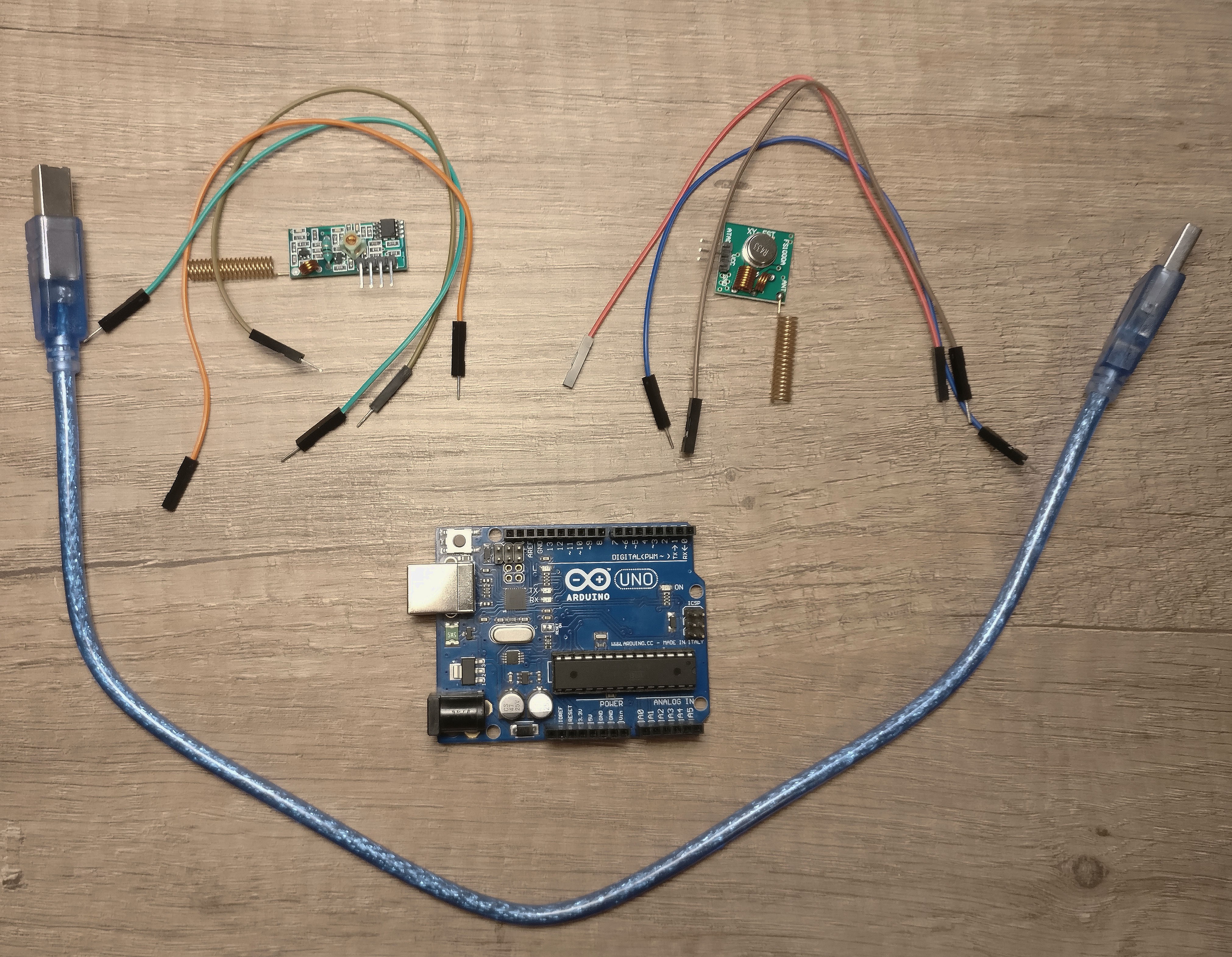
So, for the experiment we'll need:
1. Arduino UNO
2. USB cable
3. 6 male-female breadboard cables
4. a pair of 433 Mhz ASK RF module
5. a pair of 433 Mhz antennas
6. a computer with Arduino IDE installed
7. the RemoteSwitch library, it can be downloaded here
Wiring up:
1. the transmitter (the square one) goes to ground and vin and digital pin 11 of the arduino uno
2. the receiver (the rectagle) goes to ground, 5V and digital pin 2
3. plug the usb
Note: check the pictures attached to see how the pins can be identified
Uploading the code:
1. download and install RemoteSwitch library from the location above
2. select the "Retransmitter" sketch and upload it
After the sketch is finished uploading, it will sniff 433 signals and replay them after 5 seconds. And that's it with very cheap components and little work the signals from the remote control or sensors can be cloned.
Some attacker can place a small device near your home to record the signals and he can play them back to disarm the alarm.
How can we protect ourselves against this kind of attack?
* look for an alarm system that offer encryption and rolling codes for the remote control and sensors
* some systems have an alternative arm by SMS or voice call. It's safer
Step 3: Fooling door / window sensors

These sensors are made of two parts a fixed part and a mobile part. The fix part contains a circuit, and battery and something called "reed switch". This switch is very small and it lets electricity pass when a magnetic field is near, that's why the mobile part of the switch is in fact a magnet.
The main weakness of this device is it's dependence of a magnetic field. You can use a stronger magnet to keep the switch "on" even the mobile part (containing the smaller magnet) is removed....
Read more » Dan Ionescu
Dan Ionescu
 Rex Garland
Rex Garland

 HBChen-094
HBChen-094
 junkotron
junkotron