DBPOWER ELM327 Wi-Fi Interface (OBD II) "review"
just out of interest I bought one of these to play with
just out of interest I bought one of these to play with
To make the experience fit your profile, pick a username and tell us what interests you.
We found and based on your interests.
Last night the control engine light came on. 11PM, -3°C, 50km from home. Great - not. Drive home? Get towed?
So this adapter confirmed to me:
P0141 - O2 sensor heater circuit bank 1 sensor 2
= not critical = I could drive home without damaging the engine or catalytic converter
Last time I dealt with the exhaust system because of some lose/noisy part(s) I noticed that the connector of the 2nd O2 sensor (that just controls if output of catalytic converter is fine) did not latch (came off again by moderate pulling). So, most probably this is caused just by a bad connection easily fixed if there is a ramp, sunshine and +10°C instead of night and -3°C somewhere on the road.
Resetting the error flag to see if this was a one-time event did work as well.
So I can't recommend enough to get one of those adapters (better go for the Bluetooth version because of random Wifi connection problems with this specific adapter) to put in your cars toolbox.
I use an dumbphone, not a smartphone for all my mobile phone tasks and never really used Android before. Well, because I already waste enough time on the interwebs...
Long story short, I was given an already rooted ZTE blade Gen1, upgraded it to the last official Cyanogenmod version, put the Torque apk on there (appstore requires google account, I don't want one) and intalled it. Torque connects and detects the wifi obd adapter once set up. Time to connect it to my ECU...
Read more »+++ cmd> setet 4 Ok cmd> setwp ***************** Ok cmd> setssid Bordnetz Ok cmd> wificonfig SSID : Bordnetz Network Type: AP(2) Encrypt Type: WPA2-AES(4) PassPhrase : ***************** Ap's channel: 1 Dhcp Client : enable Ok cmd> saveconfig Saving Configuration to FLASH Ok cmd> reboot device will reboot... Ok cmd>
and *tadaa*
Cell 06 - Address: 00:0E:C6:00:3B:1B Channel:1 Frequency:2.412 GHz (Channel 1) Quality=48/70 Signal level=-62 dBm Encryption key:on ESSID:"Bordnetz" Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 9 Mb/s 18 Mb/s; 36 Mb/s; 54 Mb/s Bit Rates:6 Mb/s; 12 Mb/s; 24 Mb/s; 48 Mb/s Mode:Master Extra:tsf=00000000366ff4f2 Extra: Last beacon: 344ms ago IE: IEEE 802.11i/WPA2 Version 1 Group Cipher : CCMP Pairwise Ciphers (1) : CCMP Authentication Suites (1) : PSK
As found out in the previous log, the wifi module is an XLW-210D from xlwtech, running on an AX220xx compatible chip from Asix.
Rabbit hole 3 (dead end):
It is possible to get access to the source code of the reference design with the right google queries and some guessing shockingly easy (why do they include the "blabla not for public relase" note only INSIDE the source code and not in the archive file name?)... as this data is not meant to be freely accessible on the web, I won't provide it here and won't provide tips how to find it. There is no "magic" in there, as the regular function of the device is just obvious, and neither the "AppSrv" nor the demoplug source is included.
Back to Rabbit hole 1:
If AppSrv is enabled, the device spits out to 114.215.182.213:8001 every 500ms:
> 11 00 <OWN MAC ADDR>
Obviously, it wants to call home. Lets answer that call by just echoing back:
> 11 00 <OWN MAC ADDR> < 11 00 <OWN MAC ADDR> > 11 00 <OWN MAC ADDR> < 11 00 <OWN MAC ADDR> ...
This does not work, the device does not react. Lets assume the first two bytes are a command, last 6 ones are parameter. As embedded devs usually don't grab numbers from a RNG for enums etc. but use simple patterns... lets try:
> 11 00 <OWN MAC ADDR> < 12 00 00 00 00 00 00 00 ...silence....
Is it dead, jim? No! Exactly 60 seconds later, the device asks for AppSrv, this time with other content:
> 11 01 <OWN MAC ADDR> < 12 00 00 00 00 00 00 00 > 11 01 <OWN MAC ADDR> < 12 00 00 00 00 00 00 00 ...
It is not happy with 0x12 anymore. Maybe it wants more?
> 11 00 <OWN MAC ADDR> < 12 00 00 00 00 00 00 00 ...60 seconds silence... > 11 01 <OWN MAC ADDR> < 12 01 00 00 00 00 00 00 ...60 seconds silence... > 11 02 <OWN MAC ADDR> < 12 02 00 00 00 00 00 00 ...60 seconds silence... > 11 03 <OWN MAC ADDR> < 12 03 00 00 00 00 00 00 ... and so on.
Yay, AppSrv fake online :D
Another thing found out: If the payload is shorter than 8 bytes, the message is ignored. At least for the \x12 command the last 6 bytes just seem to be there for alignment and without any particular function.
Btw the source of the UDP packets is not checked by the device, as long as I sniff the data with libpcap and issue a simple
printf "\x12\x??\x00\x00\x00\x00\x00\x00" | nc -u 192.168.0.9 8001
the device is happy.
Uart communication does not seem to interfere with "AppSrv" actions in this state.
To this point, it was easy to figure out the protocol, just because there is direct feedback (read: changed or no response) from the device which "asked" for the right answer. Now the connection is there but I don't know what to ask the device for.
As the AppSrv thing is meant to be a remote-control service from smartphone/anywhere (google translator told me), there must be a command that lets us
a) write data to UART
b) read (poll) data from UART (or enable data transmission)
As this is a chip on my desk, I am sure they shipped it with the complete function and did not stop the implementation after handshaking, even if the AppSrv is offline right now...
We're in :) and the first thing to do is to rename the wifi to "Bordnetz" (German for "vehicle electrical system", but netz = network and "Bord" like in "on-board", I just like this kind of jokes):
cmd> version
mac: 000ec6003b1b
ver: 1.02.23
id : 14041601
Ok
cmd> help
Usage: quit
Usage: version
Usage: setdef
Usage: saveconfig
Usage: reboot
Usage: setssid <Maximum 31 characters>
Usage: setnt <0 = sta, 1 = adhoc, 2 = ap>
Usage: setet <Encryption Type>
<Encryption Type> 0: No Security 4: WPA2-AES
1: WEP-WEP64 5: WPA1-TKIP
2: WEP-WEP128 6: WPA1-AES
3: WPA2-TKIP 7: AUTO
Usage: setwp <WPA Passphrase, 8 ~ 63 characters>
Usage: setch <channel index>
<channel index>
0: Auto 1: 1 2: 2 3: 3 4: 4 5: 5 6: 6
7: 7 8: 8 9: 9 10: 10 11: 11
Usage: wificonfig
Usage: setwifi <status>
<status>: 0: disable wifi 1: enable wifi
Usage: serialport <baud rate> <data bits> <parity> <stop bits> <flow ctrl>
<baud rate>: 0: 115200 5: 4800
1: 57600 6: 2400
2: 38400 7: 1200
3: 19200 8: 300
4: 9600 9: 110
<data bits>: 0: 5 1: 6 2: 7 3: 8
<parity>: 0: Odd 1: Even 2: None
<stop bits>: 0: 1 1: 1.5 2: 2
<flow ctrl>: 0: Xon/Xoff 1: Hardware 2: None
Usage: ipconfig
Usage: setip <ip addr>
Usage: setmask <netmask>
Usage: setgateway <ip addr>
Usage: setdns <ip addr>
Usage: setmode <mode>
<mode>: 0: SERVER 1: CLIENT
Usage: connectype <type>
<type>: 0: TCP 1: UDP
<type>: 10: TCP Srv + Tcp Cli
Usage: setsrvport <port>
Usage: setdstport <port>
Usage: setdsthn <Host name/IP>
Usage: connstatus
Usage: setdhcpcli <status>
<status>: 0: disable 1: enable
Usage: setdhcpsrv <status>
<status>: 0: disable 1: enable
Usage: dhcpsrv <start addr> <end addr> <netmask> <gateway> <lease>
Usage: show counter
Usage: transmitsize <size>
<size>: size in byte (0~4096), default 1024
Usage: transmittime <time>
<time>: time in ms (0~1000), default 50
Usage: smartconfig
Usage: setat <flag>
<flag> =1, at cmd enabled, =0, at cmd disabled
Usage: setxap <flag>
<flag> =1, XAP is enabled, =0, XAP is disabled
Usage: setio <pin> <dir> <value>
<dir>: 0 = input, 1 = output
setio 1 0 :set p1 dir to input
setio 1 1 :set p1 dir to output
setio 1 1 0 :set p1 output to low
Usage: getio <pin>
getio 1 :get p1 status
Usage: appsrv <flag>
<flag> =1, appsrv enabled, =0, appsrv disabled
Usage: demoplug <flag>
<flag> =1, enable plug demo, =0, disable plug demo
Ok
cmd> getio 0
invalid pin
Error
cmd> getio 1
Error
cmd> getio 2
pin=2, value=1, tick=0
Ok
cmd> getio 3
Error
cmd> getio 4
invalid pin
Error
cmd> getio 5
invalid pin
Error
cmd> gerio 6
Unknown command gerio
cmd> getio 6
invalid pin
Error
cmd> connstatus
Wifi Status : Disconnected.
Socket Status: Disconnected.
Ok
cmd> ipconfig
Static Ip:
Current IP : 192.168.0.10
Current IP Mask: 255.255.255.0
Current Gateway: 192.168.0.10
Ok
cmd> show counter
Uart Rx = 248
Uart Tx = 6215
Socket Rx = 0
Socket Tx = 0
Ok
cmd> demoplug
plug demo is disabled.
Ok
cmd> appsrv
appsrv is disabled.
Ok
cmd> ssid
Unknown command ssid
cmd> reboot
device will reboot...
Ok
cmd>
cmd> quit
cmd>
cmd> wificonfig
SSID : WiFi_OBDII
Network Type: AP(2)
Encrypt Type: None(0)
PassPhrase : 12345678
Ap's channel: 1
Dhcp Client : enable
Ok
cmd> ipconfig
Static Ip:
Current IP : 192.168.0.10
Current IP Mask: 255.255.255.0
Current Gateway: 192.168.0.10
Ok
cmd> cmd>
cmd> set setssid Bordnetz
Ok
cmd> cmd> wificonfig
SSID : Bordnetz
Network Type: AP(2)
Encrypt Type: None(0)
PassPhrase : 12345678
Ap's channel: 1
Dhcp Client : enable
Ok
cmd> saveconfig
Saving Configuration to FLASH
Ok
cmd> reboot
device will reboot...
Ok
cmd>
cmd> setwifi 1
Ok
cmd> ipconfig
Static Ip:
Current IP : 192.168.0.10
Current IP Mask: 255.255.255.0
Current Gateway: 192.168.0.10
Ok
cmd> cmd>
cmd> ipconfig
Static Ip:
Current IP : 192.168.0.10
Current IP Mask: 255.255.255.0
Current Gateway: 192.168.0.10
Ok
cmd> wlanconfig
Unknown command wlanconfig
cmd> wificonfig
SSID : Bordnetz
Network Type: AP(2)
Encrypt Type: None(0)
PassPhrase : 12345678
Ap's channel: 1
Dhcp Client : enable
Ok
cmd> quit
Lets...
Read more »The chip with removed label may be an AX220XX compatible device, as its MAC is from this manufactuer. It offers a web interface, but only delivers an empty index.htm on port 80. Port 35000 bridges to the PIC microcontroller. Do not send "+++ return" command over tcp to port 35000, because this leads to message ping-pong between the two controllers.
trying the ethernet vector:
Open ports are:
80, tcp, http (empty index.htm, else http404)
67, udp, dhcps
49153, udp, ???
35000, tcp, uart bridge
For AX220XX there are different reference designs availabe, e.g. over here: http://www.uconnect.com.tw/WMS.html http://www.uconnect.com.tw/files/WiFi_to_serial_command_set_V1.pdf
The AXR2W config tool is availabe in the WA-232B-toolbox.zip over here: http://www.usconverters.com/index.php?main_page=product_info&cPath=70&products_id=404 (requires msports.dll to run under wine), but the chip does not respond. The magic "discovery" string this tool uses is ASIXXISA[0x0e] and is sent over UDP to port 25122.
replaying that magic packet with:
printf "ASIXXISA\x0e" I nc -u 192.168.0.10 49153 -p 25125
did not work...
btw: leaving out the "-u" switch and just running the command on the tcp uart port leads to direct uart/CAM access from shellscripts...
As a summary, It looks like they locked down the chip to prevent mods from the ethernet side, but it still got an exposed uart and it is possible to dump the flash chip contents.
This pdf contains a list of commands the AX220XX accepts over UART, including the "+++" command. As my "unknown" chip reacts to the "+++" command, it is likely that the other commands work, too and -in fact- it is an AX220XX compatible chip.
I won't link to leaked documents from the manufactuer over here, as you can do your own google search. If you try "bootloader" or similar terms together with the chip name, you'll find some pdfs and source code on chinese document sharing platforms ;)
Btw. the whole device consumes 120mA at 12V (1.44 watts), the drop of 12 down to 3,3 V at this current wastes ~1 watt, which makes the linear regulators quite hot. Power safe mode of ELM327 saves about 10mA... as the OBD2-port is connected to the car battery regardless of the ignition switch state, I can only warn to leave these adapters connected while the engine is not running for longer periods of time.
Things to try now:
- wlan is unencrypted, so kismet will show anything the device sends out during startup
- uart access with usb-ttl-uart adaptor
btw. just ordered a cheap 3.50Eur "usb car adaptor" which runs on a step-down converter to replace the lm7805 on the main board, keep the device cool and make it live longer.
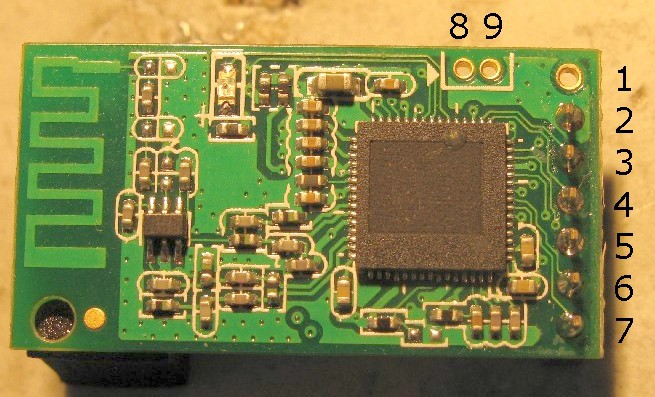
Pin 1-7 are 2mm pin header.
To get access to the UART (and power the module), a normal 3V3 or 5V ftdi cable is suficcient. Make sure to use 3V3 to power the module.
The device consists of a red main board and a green wifi addon board:
The three electrolytic caps are all 16V rated and on "car +", +5V and +3V3 rails. The chip near the conenctor is a Microchip can controller, the chip on the left is a Microchip pic 18F, which does the CAN-UART translation in the same way as the "original" ELM327 would do. UART is exposed on the pin header in the center to go to the wifi board. The unpopulated parts on the top edge of the board (SO8 IC U11, diode D4, and inductor L1) form a step-down buck converter... but they populated the lm7805 - d'oh!
Not much on the bottom layer: 7805 and 3V3 linear (!!!) regulators and a footprint for a bluetooth module (not populated):
Can transceiver: MCP2551I
PIC microcontroller: PIC18F25K80, supported by PicKit3
The solder job is ok, except solder balls all over the place:
The Wifi-module consists of just one big SoC (part name removed :( ), passive differential-to-single-ended convertion circuit and a TX/RX switch for RF stuff. Footprints for PI filter is present, but not used.
On the bottom layer, a 4Mbit SPI flash holds the software (interface pins exposed :) ), a quatz drives the clock and a LDO (?) does additional local voltage regulation. A pad to mount an U.FL connector (or similar) is present, but would need a resistor on the top side to be moved one pad.
SPI 4MBit flash: 25L4006E
Wifi SoC: unknown type, 60pins (T)QFP package
TX/RX switch (right to antenna, left/bottom are TX/RX paths)
Next step is to clean up the red main board and remove the loose solder balls, then power it up using a lab PSU and begin probing/hacking
Create an account to leave a comment. Already have an account? Log In.
Through all your explorations of the ELM327 device, have you found any way to enable the web interface like some previous revisions of the ELM327 had? I need to change a specific setting and I don't see that as a UART command.
Serial Framing Timeout or Data Trigger Timeout
Good morning to all
sorry for my english.
I have one question about the electrical RS232 connection. Can you show me a diagram?
I just have a ttl rs232 and I have the 3.3V power supply. Tell me if it is correct:
PIN 2 with GND
PIN 5 with 3.3V
PIN 3 with TX
PIN 4 with RX
Is it correct?
Thanks,
nowire
hi rawe,
great review! thanks a lot!
I've got a problem with my elm327 wifi interface, maybe you can help me out. I changed the baud rate to 57.6kbps which doesn't work well with this device. I can't send/receive anything any longer except garbage.
Are you aware of any way to factory reset this device? Would it be possible to solder some rs232 cable directly to the device to reset the baud rate? I tried connecting pin28 and ground to reset it but that didn't work. Do you have some idea?
thanks a lot!
hi mc_stinzel,
I will assume your "wifi elm adaptor" is the same type as mine. There are different variations of these devices but I can only compare to the one I own.
Combining your info leads me to the conclusion that you changed the baud rate of the elm327 via wifi. This lets the elm327 talk faster, but not the wifi-uart bridge chip which runs on the same baud as before = baud mismatch = nonsense output via wifi.
Connecting pin28 to GND and then applying power to the circuit should bring the elm327 back to default configuration of 38400 baud. As this is the default baud of the wifi module everything should be "back to normal". I understand the reset procedure as follows:
1. power off board
2. add a connection between pin28 and GND
3. power up board. elm327 sees the connected pin and clears its config
4. power off board
5. remove connection pin28/gnd
6. back to normal
(not verified/tested myself) If this does not work, it is time to have a look at the signal lines to check what the two processors talk to each other.
Be aware of the difference between UART (just the encoding of the information as "universal asynchronous receiver / transmitter"), RS232 (UART but with +/- up to 15 volts signal level) and and "CMOS UART" (UART but with chip voltage logic level e.g. 0 and 3.3V for 0 and 1).
(from wikipedia.de, hac.io does not let me just paste the link:)

As I don't know the tools you have handy the simplest and cheapest way to check what is going on would be to hook up a cheap usb-uart adaptor to a computer and just connect the "RX" pin and ground of it to the elm327. This way you can listen on one of both channels (wifi module to elm327 and the other way round) depending on the signal pin you connect the usb-uart-adaptor RX pin to. This way you know the signal tapping does not modify the communication and the usb-uart-adaptor works right. plugging out the wifi module, connecting the TX pin and sending the elm327 a baud set command would be the next step.
Just let me know if there are other Qs or if you managed to fix (or break ;) the device.
Cheers,
rawe
hi rawe,
thanks for this long explanation and your help.
I tried to reset the unit exactly the way you described it but it didn't work. So I think the only way will be to reset the baud rate manually. The question that came to my mind while reading your response was that if I want to continue using the wifi module, will I ever be able to raise the baud rate to something higher than the default one? I'm asking cause the reason I raised it in the first place was that I weren't able to capture all the data from the can bus. I've received data errors followed by the well known 'buffer full' error.
If I hook up a serial connection directly to the elm327 raising the baud rate shouldn't be a problem, right?
I'm (unfortunatly) not really the hardware/electronical guy, more the software kind, but if I've understood you correctly, the difference between these devices lies in the 'modulation' of the signals? E.g. normal RS232 has different voltage levels than cmos uart?
At the moment I only have a cheap usb to serial converter. If I connect the rx pin of my usb to serial converter to either the rx or tx pin of the elm327 device I should be able to see the data they exchange? Or further thought as you already mentioned, how would it be possible to spare the wifi component out and 'convert' the elm to a usb type one? Must I use an usb-uart adapter or can my usb to serial cable be used? which pins should be connected exactly?
Cheers,
mc_stinzel
hi mc_stinzel,
You are right about hooking up directly and the "modulation".
If the usb to serial converter does "logic level / cmos uart" this should work.
If it does "rs232" it is not compatible because a logic "0" is 0V and a logic "1" is 3.3V (or 5V) for the ELM327 but a logic "0" is "3V up to 15V" and a logic "1" is "-3V down to -15V" for a computer/rs232 device. If you plug them together they do not understand each other plus too high voltages are applied to a chip that can handle only 3.3 or 5V which might damage it.
See http://www.ftdichip.com/Products/Cables/USBRS232.htm for a list of common usb-uart adaptors.
The "cmos level" or "logic level" adapters contain just one single chip that speaks USB on one side and provide "logic level uart" signals on the other side:

The "RS232" cables contain an additional chip that converts the "logic level uart" signals of 0/3.3V to +/- 15 V:
(Schematic over here http://www.ftdichip.com/Support/Documents/Schematics/FT232R/UC232R%20Schematic.pdf )
Of course you could buy or build a board to convert the signals back or just rip out the signal level converter chip on your usb serial adapter and connect directly.
To talk to the elm327 directly, plug out the wifi module and just hook up GND (because it is the reference for the signals), RX and TX.
As the GND of the ELM327 board is connected to car chassis and there is no isolation between the uart GND, usb GND and laptop GND it might be problematic to run the laptop on its own power supply powered by an inverter etc.
hi rawe,
thank you, I think I've got it now :-)
thanks to your instructions I were finally able to fix it today. I've transformed it into an USB version for now :o)
I then tried to increase the baud rate to the maximum supported (500kbps) and now the garbage is back again, yay.
if it is of any help, I used the following commands: atpp 0c sv 08, atpp 0c on
What can be the reason for this? Maybe the chipset is a cheap one and doesn't work well with this 'high' rate? Any idea how to fix it now? :-)
I tried raising the baud rate in steps and every other rate worked without a problem.
Regarding the factory reset. It may be a dumb question but which PINs exactly do I have to connect? I've got the exact same device as you regarding to the pictures. PIN 28 should be - according to the pinout of the chip - the top left pin? (when holding it with the obd2 plug to the left) And ground can be any ground on the board, so e.g. pin 5 of the odb2 plug or the one from the wifi module (pin 2)? Is this correct?
cheers,
mc_stinzel
Well, at least I've reconfigured the wireless chip to be used as a wireless serial connection to my old netgear wgt634u router :-)
thanks to your pin layout this was quite easy to accomplish.
cheers
mc_stinzel
hi rawe,
I hope you are still following my self-conversation :-)
Just wanted to tell you I found the problem. It was the faulty windows driver for the pl2303hxd chip in my usb uart cable. After retrying it on my raspberry pi it just worked again :-)
source: http://forum.43oh.com/topic/3873-serial-at-500kbps/
cheers
mc_stinzel
Hi Rawe great info>
I put mine AP mode it got stuck at HEX 10 digit password instead of ASCII WPA2PSK which the AP kicks it off i tried hours and different combination i came to the conclusion that I need a serial header connection or some sort of factory reset of the WiFi chip< is there anything I can do? its the older version with the PCB separate from the WiFi module .
I tried shorting GND to RST on the WiFi module UARTO , for 30 seconds, and 30 seconds while powering it up.
here are more pictures of the unit
https://forum.allaboutcircuits.com/threads/how-do-i-reset-this-wi-fi-pcb-module.177225/
Become a member to follow this project and never miss any updates

 h4rdc0der
h4rdc0der
 Ruslan
Ruslan
 Blecky
Blecky
 Remi Serriere
Remi Serriere
Hi Rawe great info>
I put mine AP mode it got stuck at HEX 10 digit password instead of ASCII WPA2PSK which the AP kicks it off i tried hours and different combination i came to the conclusion that I need a serial header connection or some sort of factory reset of the WiFi chip< is there anything I can do? its the older version with the PCB separate from the WiFi module .
I tried shorting GND to RST on the WiFi module UARTO , for 30 seconds, and 30 seconds while powering it up.
here are more pictures of the unit
https://forum.allaboutcircuits.com/threads/how-do-i-reset-this-wi-fi-pcb-module.177225/