Many people use the same password for different online accounts. Even if the password is very strong, hackers don't need to break into your very secure financial and other important accounts directly. They can attack a weaker website, such as a web forum or subscription service, and use the password they stole from that website's database to steal your identity and log into any of your online accounts.
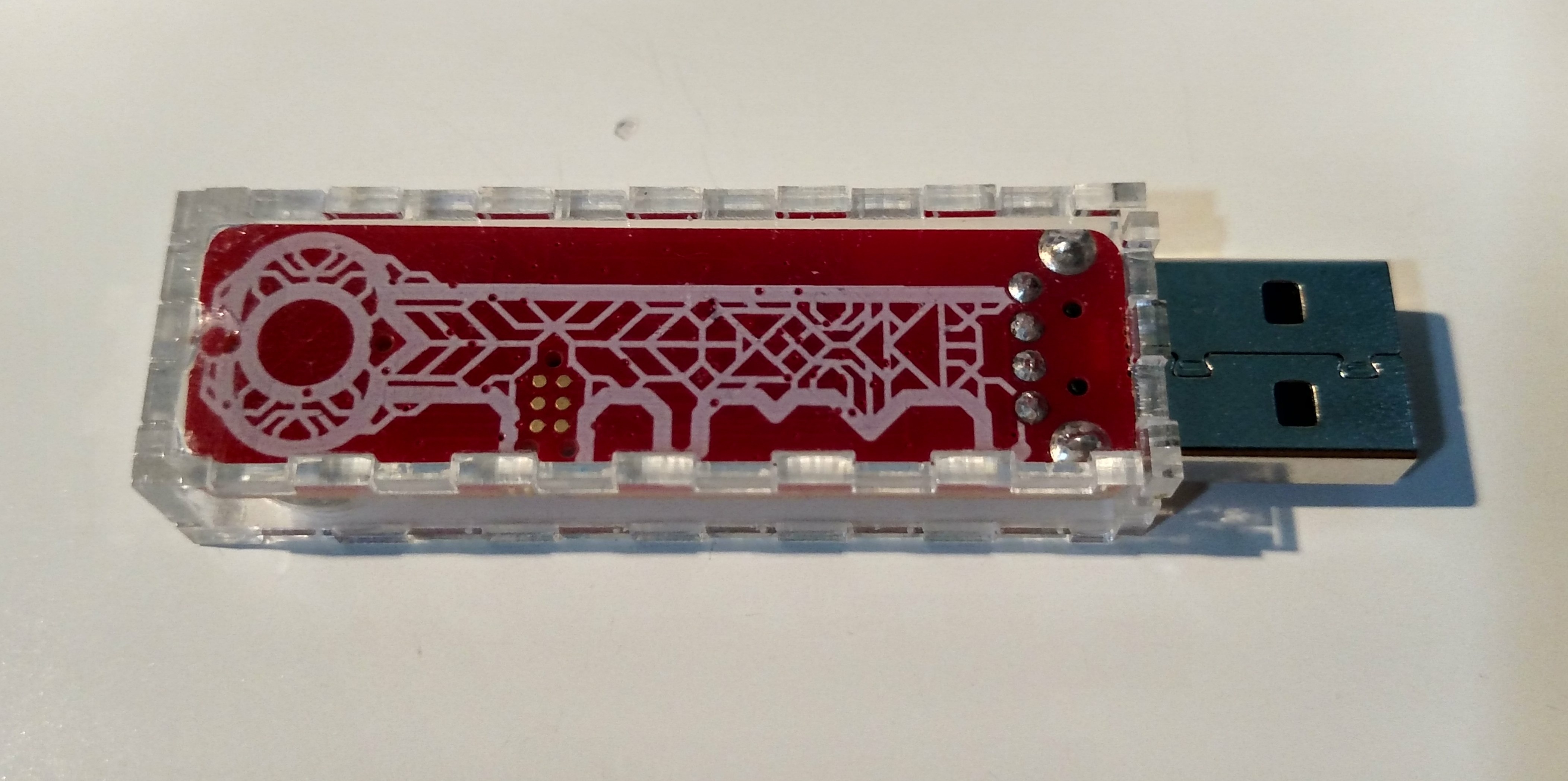
Both physical and electronic security are difficult skills to master, but most would agree that it's a bad idea to use a single key for every real-world lock you own. So why would you use the same digital key for all of your electronic locks? Many people complain that it is difficult to remember multiple passwords; in the real-world, you don't need to remember how every key on your keychain looks like. So I thought: what if you could have a keychain that keeps your digital keys for you? Zamek is the answer.
I turned to the physical keychain for inspiration, as a physical keychain is already very easy to use. When you need to unlock something, you choose the right key, insert it into the lock, and turn.
Zamek was designed to open your electronic locks as easily as a regular key opens physical locks, with an additional layer of security in case someone other than yourself picks up your digital keychain. The process can be described as:
1. Unlock your Zamek using a security PIN you choose
2. Use Zamek's joystick to change the account displayed on its screen to the one you wish to unlock
3. Insert the Zamek into your computer's USB port
4. Press the joystick to enter the password for the account
Zamek will type in the currently selected password into any field on your screen you select. If there is no USB port available, you can read the password for the account on Zamek's highly visible OLED screen and type it in manually.
Entering your account information into Zamek is intuitive and simple. After you enter your information once, it is stored permanently on Zamek's built-in memory. Your information is encrypted with an industry-recognized AES cipher, which means that if your Zamek is ever stolen, criminals will not be able to extract your information.
Zamek was designed to be your electronic key to the digital world. Smaller than a car remote, it easily clips to your keychain and can be carried everywhere. It features a highly visible screen and a long battery life, which is topped up every time you plug Zamek into your USB port. The joystick is comfortable to use, and the interface is intuitive enough to not require an instruction manual after the first set-up. Additional features currently in consideration are secure formatting and backup/restore options.
All the code and schematics for Zamek will be published under an Open Source license. This mean that anyone can read, validate, and critique the design of any part of the Zamek openly. My desire is that the Open Source process will lead to a device which is ultimately more secure, completely trusted, and reproducible in case I am not able to produce these in the future.
Lastly, Zamek is completely yours to own and use. It protects your data in a personal, respectful, and dignified manner: Zamek does not "phone home" to any remote servers, and it does not store any information anywhere other than its secure memory. Your information will never be anywhere but in your pocket.
 jareklupinski
jareklupinski To make it waterproof, it will use two hall-effect sensors to read an external bearing ;)
To make it waterproof, it will use two hall-effect sensors to read an external bearing ;)














 Ulrich
Ulrich
 Victor Dedios
Victor Dedios
 megazoid
megazoid
 Chaz
Chaz
Hey Jarek, I'm new to this project, got across it on Youtube and wanted to know if it is already available to buy or if everyone has access to all things needed to create one. I know there is a git repo but it is complete to send to someone to manufacture it and when it arrives will everyone be able to make one with not much effort or do we need to finish some things to get it to work? Thanks!